Saturday 21 December 2019
Saturday 14 December 2019
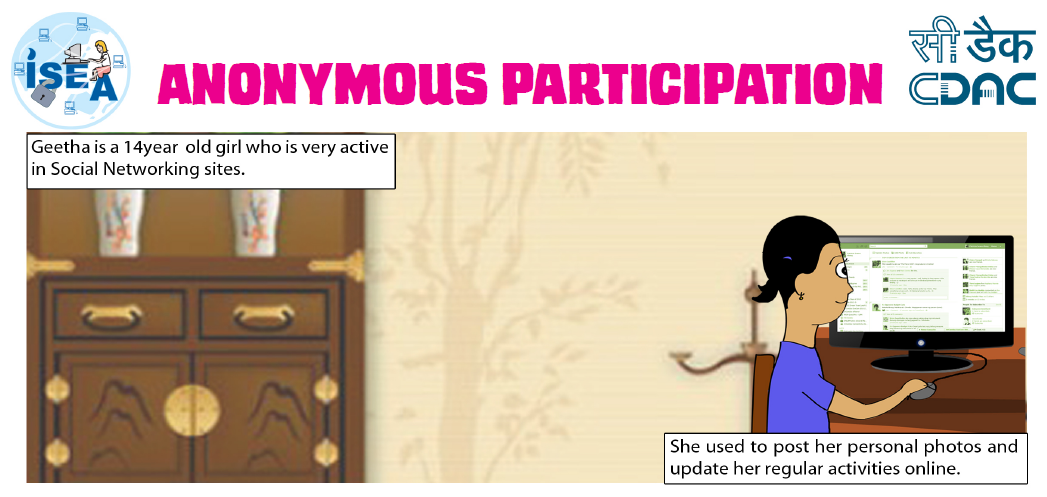
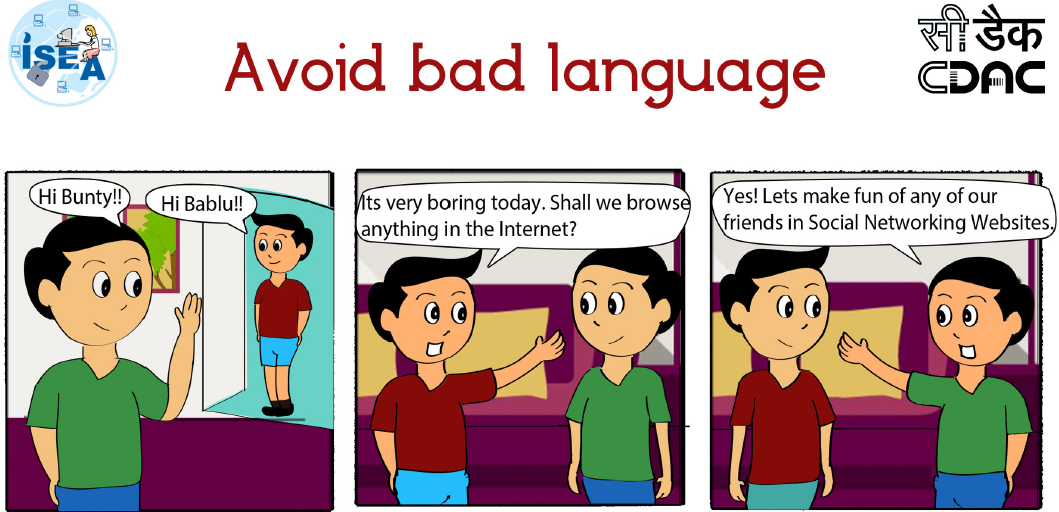
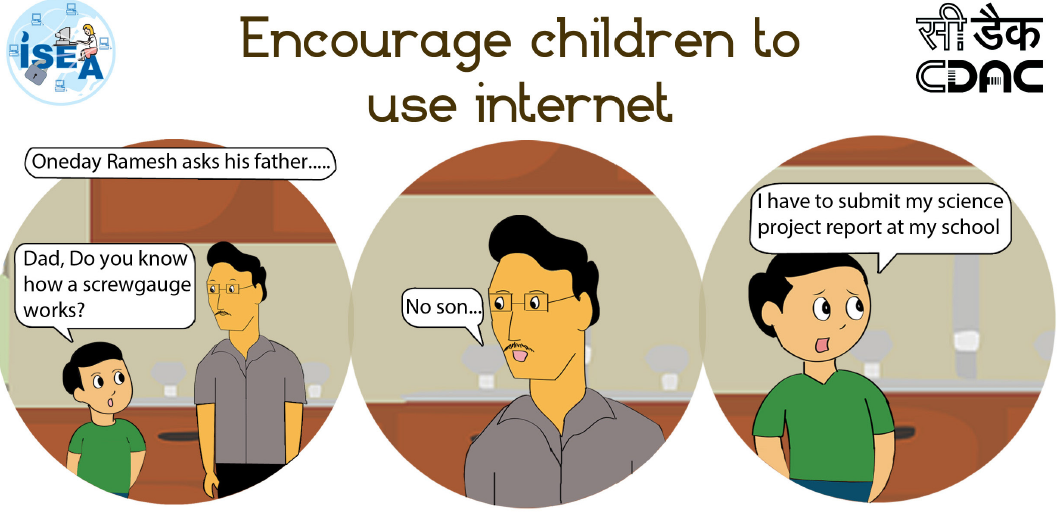
ISEA Cyber Safety Cartoon Stories - Must Read for Kids to Learn about Cyber Safety
Friday 13 December 2019
Cyber Threats - Self Assessment
Thursday 12 December 2019
Tuesday 10 December 2019
Cyber Threats to Children
According to statistics released by the National Crime Record Bureau (NCRB) on October 22, 2019 Cybercrimes in India almost doubled in 2017. Karnataka had the highest rate of cybercrime with Bengaluru registering the most number of cybercrime cases in 2018 , followed by Assam, Telangana, Maharashtra, and Uttar Pradesh. India ranked third in the list of countries where the highest number of cyber threats were detected, and second in terms of targeted attacks in 2017, according to security software firm Symantec.
Let’s see what are some of the online threats that we should be aware of.
Malicious Content
One of the issues that we should be careful about is the Malicious Contents.
• Malicious content means documents or programs infected with viruses, or websites that try to infect your computer with virus. The infected site will cause your computer to be infected and these virus may steal your personal information, delete your files, or encrypt the data on the victims computer, then asking for payment to get the data. Hope you might have heard about the Wannacry ranswomware attach in 2017.
• Most often browsers like Google Chrome or Firefox prevents you from accessing such infected websites displaying a warning message. Whenever you see such warnings from the browser, do not proceed to visit the website.
Obscene Content
Similar is the case of Obscene Content online. There are a good number of shock sites on the internet. Shock sites mean the sites that have content with high shock value material that includes pornography, violence, racist, hatred, profane, vulguar and other provocative materials.
•There may be visual with images and videos or verbal with profane languages or hate speeches. Videos of violence, murder, suicide and the like are being shared widely on social media now days. Unfortunately, our society, including the adults, seems to enjoy such violent content. If you receive such videos or files just delete them. Never watch them or forward them. Such content may have severe psychological and emotional impact on the viewers.
Also think about the violation of the rights of the victim or the victim’s family. How it will affect them when the photographs/videos of the violent deaths/accidents of their beloved one are being circulated over the Internet, reminding them of the tragic incident.
Malware
• Malware is computer software that is installed without the knowledge of permission of the victim and performs harmful actions on the computer. These software may personal information from the computer and send it to the attacker. Your computer may get infected when you download email attachments or try to install freeware software that you download from the internet.
• The infected computer may be used a ‘botnet’ to perform attacks on other computers or to mine cryptocurrency. A botnet is a number of Internet-connected devices, each of which is running one or more bots.Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allows the attacker to access the device and its connection.
Online Scams
Another common threat that people fall prey to are online Scams.
• Have you got an email from a Nigerial prince or an African accountant ready to share their fortune (worth millions) with you?
• Or an email offering scholarship to study abroad? Such techquiques are adopted by the fraudulent people to get important personal information and to extract money form the victims in the form of service charges or advance for getting the scholarship or lottery amount.
• Always remember, if an offer sounds too good to be true, it probably isn't true
• Don’t believe in offers that offer too much
It is quite unfortunate that even the educated people fall prey to such scams. If you go through the newspapers, you will find many stories of such scams.
Online Predators or Cyber Groomers.
Another serious issue, as far as childrens are concerned, is the presence of Online Predators or Cyber Groomers.
• An online predator is someone who sexually exploits a child over the Internet. Online predators normally hide their identity and pretend to be someone that the child may think safe.
• In cyber grooming, the online predators befriend the children through social media and builds an emotional bond. These predators need not be strangers. Even known people, including relatives and family friends may try to exploit a child. They try to attract children into sexual conversations and also persuade to meet personally. They may also send obscene content to the child and ask children to send pictures of themselves
• Chat rooms, instant messaging, Internet forums, social networking sites, mobile phones, and video game consoles have issues with online predations. If you ever come in contact such people, always report such cases to your parent or teacher immediately.
• Keep in mind that people are not always who they say they are.
Cyber Bullying
Cyber Bullying is another serious online threat. India ranks at number 3 in the list of online bullying cases as per the survey conducted by Microsoft in 2012 in 25 countries Cyber bullying is the bullying that takes place on digital devices or through digital media
We will be having a separate discussion on cyber bullying where we will discuss this in detail
Digital Privacy & Identity Theft
Now let’s take a look at Digital Privacy & Identity Theft
Are you wondering how a student will be affected by identity theft? Personal information is a hot commodity that has huge demand and can be monetized. You can have a look at the news report regarding the case where the data of hundreds of thousands of applicants who took the National Eligibility and Entrance Test (NEET) in 2018 are made available online for sale. If you find it unbelievable you can see an email we have received which offers personal information of various categories of students for sale. How do they get these information? Be careful when you filling online forms or registering on various websites that offers to provide CBSE question papers, scholarship information and other materials. There may legitimate and free website that may offer similar materials without asking your personal information. Avoid the website which ask you to provide your personal information to access content. If you have to provide such information, make sure to read their privacy policy.
• What are the information we should not provide?
• Never provide your personal information like your school admission number, mobile number, parental details, aadhar number etc. online
• Also Do not post any compromising photographs online – remember what we have learned in the Digital Footprint session regarding the images posted. Even if you delete it later, it may be available some where on the internet
• Don’t fall prey to online lucky draws, fake offers and fake tests that ask you to provide personal information to register
• Try to avoid Public Wi-Fi and only Use Legitimate networks to access internet.
• It is also advisable to Disable auto-connect feature of the laptop and smart phones.
• Turn on firewall on your computer and install antivirus. Update your operating system and antivirus regularly.
• Don’t forget to Logout after use on public systems
Techniques to Steal Personal Information
Now, let’s see various techniques to steal personal information. Most common method is Phishing.
Phishing is an attempt to fraudulently obtain sensitive information through e-mails directing you to enter personal information on a website. The victims are contact through e-mail that seems to be from a legitimate company or business asking them to take immediate action for getting some financial benefit or to protect their information.
They may have malicious attachments and links. The attachments may install malwares on your computer. The links may lead you to phishing websites. So never click on the link, if you are suspicious. How can we identify phishing messages. One way is to look at the email address – the email may not be from a public domain like gmail or yahoo. The mailid and the display name may not be related at all. Don’t be fooled if you see the official log inside the mail, anybody can embed a logo inside the mail.
Another way to identify such mails are to look at the content. There will be grammatical errors in the mail. Also there will be some kind of urgency in the message. It will ask to respond or take action immediately
Pharming
Pharming is the technique to redirect a website's traffic to another, fake site. The attackers install malicious code on the victim’s computer. So when you are trying to visit a website or doing an online search your browser may take you a malicious website.
At a higher level this can happen on a server also where the webserver of the website you are visiting is infected.
Smishing and vishing are also techniques used to extract information.
Smishing (SMS phishing) is a type of phishing attack conducted using SMS (Short Message Services) on cell phones.
Just like email phishing scams, smishing messages typically include a threat or a temptation to click a link or call a number and hand over sensitive information. Sometimes they might suggest you install some security software, which turns out to be malware.
Vishing (voice or VoIP phishing) is another tactic in which individuals are tricked into revealing critical financial or personal information to unauthorized entities by voice email, VoIP (voice over IP), or landline or cellular telephone using fake caller ids.
These are mainly used to get credit card details and account details
Cybersquatting
Another interesting technique is Cybersquatting. Though cybersquatting targets companies or businesses, we may have a look at these techniques also to learn about the technique.
A cybersquatter is someone who registers a domain name in bad faith and intent to profit from the goodwill of a trademark belonging to someone else. How does this benefit a cyber squatter? We have learned earlier about trademarks and copyrights. If someone who is not a trademark holder registers a domain name that includes a well-known trademark, they may be cybersquatting. They do this hoping to sell the domain name to rightful owner at a later stage to make a huge profit.
An interesting case on cybersquatting is the case of Microsoft when they filed a case against a Canadian teenager by the name of Mike Rowe. What Mike did is he created his part-time web design business and registered his domain as, MikeRoweSoft.com, that sounded too similar to Microsoft.com. Microsoft offered to pay him $10 compensation to get the domain name, but Mike Rowe asked for
$10,000. Microsoft filed a case to WIPO.Because of his intent to profit from selling the domain to Microsoft, it was held to be cybersquatting and Rowe was handed a cease and desist order by the WIPO.
Typosquatting
Another method of cybersqatting is Typosquatting.
This technique employs similar urls for popular websites and depends on the typing errors of users to get traffic to their sites. This one we should be aware of as it may affect us also. A well known example is facebok.com with a single “O”.
To avoid this, bookmark the sites you use often (using the “Bookmarks” or “Favorites” function in your browser) rather than typing them in the address bar.
Combosquatting is a newer form of cybersquatting that combines a popular trademark and a string of words or phrases with the use of hyphens. Combosquatting is a technique used in many phishing email campaigns. If a customer sees the trademark of a brand they know and trust when they look at the email address of the sender, they will be inclined to follow the link.
Eg. Yahoo-security.com Let’s be Cyber Smart!
There are so many cases of cybersquatting reported in the media. Can you find out few interesting cases?
Hour of Code
 Library is organising Hour of Code events in connection with the Computer Science Education Week joining the global movement to demystify "code", to show that anybody can learn the basics, and to broaden participation in the field of computer.
Library is organising Hour of Code events in connection with the Computer Science Education Week joining the global movement to demystify "code", to show that anybody can learn the basics, and to broaden participation in the field of computer.